The first thing that comes to mind when you think about payment gateways? It’s the payment gateway risks attached to your financial information, right? As with all other online businesses, payment gateway risks are inherent.
Today, we live in a world where online purchases happen seamlessly. It is as simple as placing the order, and your money is transferred effortlessly from your account to the seller almost instantaneously. These secure online portals act as intermediaries between your preferred payment method (credit card, debit card, etc.) and the merchant’s bank. They handle sensitive details securely, ensuring a smooth transaction for both you and the seller.
But payment gateways are much more than just convenience. We’ll dive deeper into their crucial role in safeguarding your financial information. We will also talk about mitigating the payment gateways risks and facilitating the growth of online businesses.
Payment Gateway Work Model
Payment gateway technology captures payment information (e.g. card details, bank details, etc.) and transfers it to the merchant’s (acquiring) bank, securely authorizing card or direct payments.
Here’s a simplified flow of how a payment gateway works
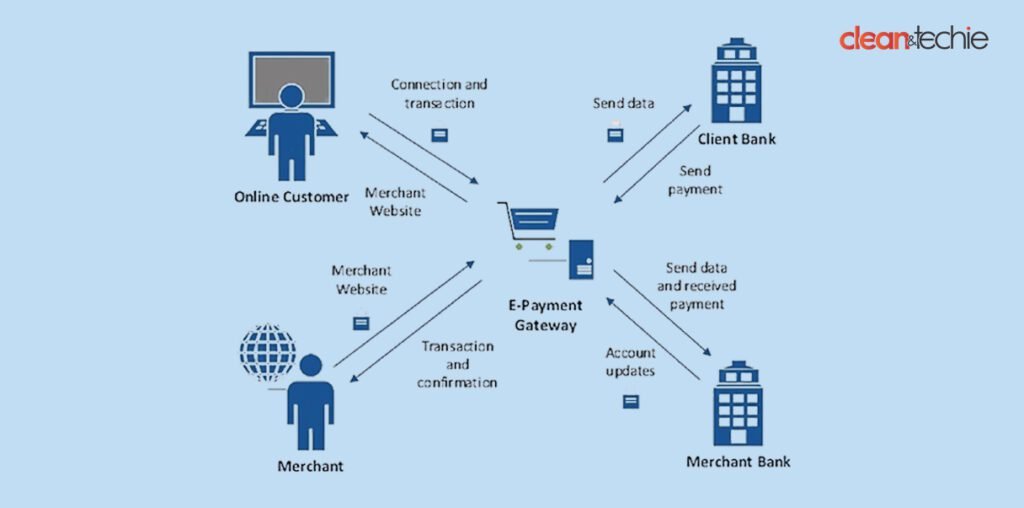

Payment is initiated
The customer uses the allotted space to enter payment details on the merchant’s website. A well-known example of this is e-commerce.
Encryption of data
This information is then converted into machine language, secured by encryption, and sent to the payment gateway.
Request for authorization
The collected information is then forwarded with the transaction data to the acquiring bank by the payment gateway.
Response from bank
The payee bank processes this transaction and reverts with an authorization to the payment gateway.
Completion
The payment gateway collects this response and sends it to the merchant’s website, completing the transaction.
Threats to Payment Gateways
Data Breaches: Cybercriminals target payment gateways to steal sensitive information such as credit card numbers and personal details.
1. Unauthorized Access
A network intrusion often starts with unauthorized access.
This can happen through things like exploiting weak passwords, software vulnerabilities, or even physical security breaches. Once the intruder gains access, he can move laterally to reach the payment gateway and its treasure trove of financial data.
2. Phishing Scams:
Phishing scams are a deceptive tactic where attackers use emails or fake websites to trick users into revealing sensitive information like login credentials. Once obtained, these credentials can be used to gain unauthorized access to the payment gateway.
3. Malware and Ransomware Attacks:
Malicious software (malware) can wreak havoc on your systems. In the context of payment gateways, malware can disrupt payment processing or even steal credit card information. Ransomware is a particularly nasty form of malware that encrypts your data, making it inaccessible until a ransom is paid.
4. Stolen Credentials:
Let’s face it, data breaches happen. If your login credentials are compromised in a separate attack, cybercriminals can use them to access your payment gateway unless additional security measures like multi-factor authentication are in place. By understanding these common threats, you can take steps to safeguard your payment gateway and protect your customers’ financial information.
5. Hacking
Hackers target payment gateways through various methods, like sneaking into communication channels (man-in-the-middle attacks), exploiting software weaknesses (SQL injection), or tricking users into giving away credentials. Once inside, they can steal sensitive data, alter transactions, or even lock you out with ransomware. Be vigilant and choose secure payment gateways to safeguard your financial information.
How can we mitigate these threats?
Anti-virus and anti-malware software
Installation and maintenance of an anti-virus and anti-malware software to keep it up-to-date on all systems connected to the payment gateway are absolutely necessary.
Access authorization
Ensuring the right people have access to the systems will protect the systems from any kind of digital forgery. Payment gateway risks related to unauthorized access can be controlled.
Strong passwords and MFA
A complex password (a combination of capital letters, and small along with special characters) is always recommended. Implement Multi-Factor Authentication (MFA) for all accounts. MFA Implementation acts as an extra verification step beyond just a password.
Vulnerability Management
Regularly update the software and firmware of the systems that are in use to keep a check on vulnerabilities. Plan the vulnerability scans to identify and address weaknesses before attackers can exploit them.
Network Security and Security Audits
Utilize firewalls and intrusion detection and prevention systems (IDS and IPS) to monitor network traffic and block suspicious activity. Segment your network to limit access to critical systems, like the payment gateway. Perform timely security audits to assess the overall security health of the systems and identify areas for improvement.
Employee Training
Educate employees about phishing tactics and how to identify suspicious emails and websites. Teach them to never share login credentials or click on untrusted links.
System Backups:
Regularly backup your data and systems to ensure a clean recovery point in case of a ransomware attack.
Session Timeouts:
Set session timeouts for user inactivity to automatically log users out after a period of non-use.
Conclusion
As the backbone of online transactions, payment gateways play a crucial role in the seamless transfer of funds between customers and merchants. However, with the rise of digital payments comes an increase in the payment gateway risks and threats to these essential systems.
By implementing these measures, you can significantly reduce the risk of hacking and protect your payment gateway from unauthorized access and data breaches. Remember, security is an ongoing process, so stay vigilant and adapt your strategies as new threats emerge.
Also Read: Is Buying Backlinks a Good Idea?